With June upon us, it’s a good time to take a look at technologies to watch for the next-gen enterprise. Dion Hinchcliffe of ZDNet has a nice list of things business and IT leaders should be considering in their annual budgets. The challenge might not be
what to spend money on, but how to get a bigger budget with so many technologies starting to mature.
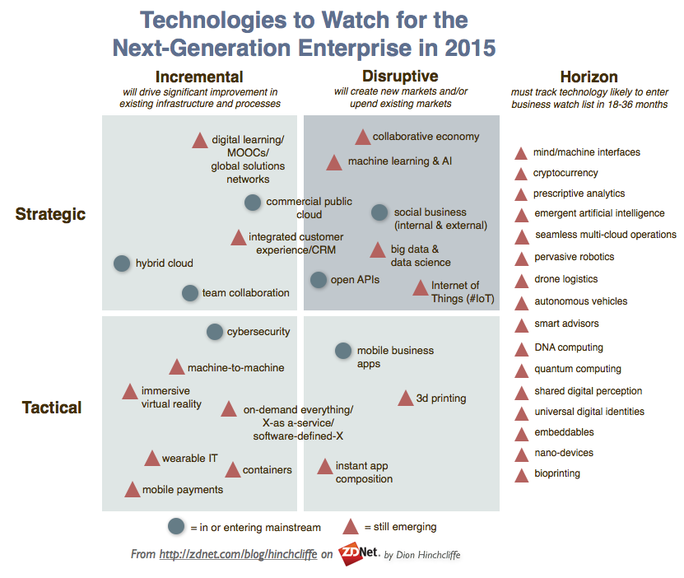
The article has a quadrant chart crowded with technologies split into strategic/tactical and incremental/disruptive. Beyond that, Hinchcliffe categorizes the innovations into “in or entering mainstream” and still emerging. And just to be comprehensive, there is a column for what’s beyond emerging to tech that’s still on the horizon.
A couple of the topics applicable to Uplogix include Machine-to-machine (M2M) and cybersecurity:
The ability of an Uplogix Local Manager (LM) to monitor network and communications devices and take actions automatically really is an example of M2M. We’ve just been doing it since before anyone coined the phrase.
Hinchcliffe uses a “smart” refrigerator as his example. While having your fridge report on its contents and their levels to a shopping app on your phone is kind of fun, an LM detecting and recovering a router from ROMmon state or automatically switching satellite antennas on a ship when the primary enters a blockage zone can really save your bacon.
Cybersecurity is a broad category, but clearly holding top-of-mind status with IT groups and the C-suite. The article says cybersecurity is the only tech topic that IT and business executives are fully aligned on, with organizations upping their security budgets by an average of 41% last year.
It’s widely accepted that the greatest security risks are from insiders, whether from intentional exploits or, more commonly, from user errors that leave businesses vulnerable to outside attacks.
Uplogix is a closed Linux appliance, meaning that it’s a secure device that locks down an often-overlooked insider risk — the console port. With continuous monitoring and logging of every key stroke and device response, Uplogix can close abandoned sessions with devices and granular authorization ensures only the right people have access to the equipment (and commands) that are appropriate.
So when you think about Uplogix and the proven, yet next-generation capabilities of Local Management we’re pretty much right in the crosshairs of the tech to watch quadrant.